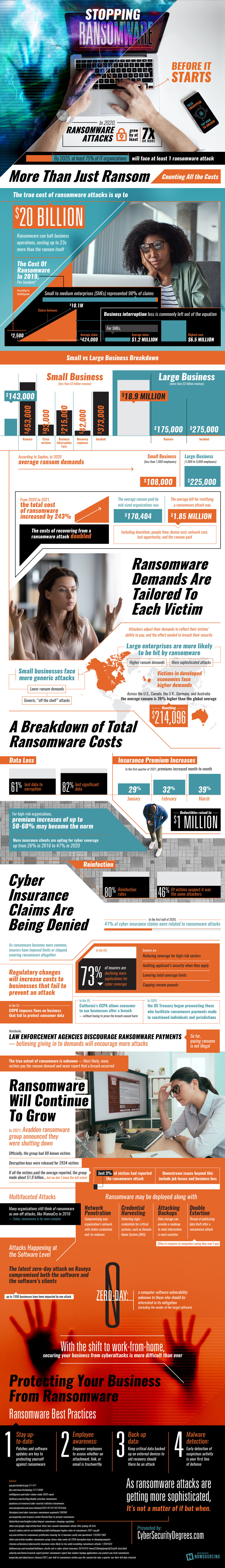
AWS is the leading cloud provider, but new research shows that 90% of S3 buckets are vulnerable to ransomware attack.
AWS is the leading cloud provider, and has a good reputation for security and reliability. Despite that, however, research from Ermetic shows that identities pose a serious risk to security and open buckets up to the possibility of a ransomware attack.
The IT community regards S3 buckets as extremely reliable. What organizations typically don’t realize is that the biggest risk to this storage comes from another source: identities. A compromised identity with a toxic combination of entitlements can easily perform ransomware on an organization’s data. Recent Ermetic research found that ransomware-vulnerable combinations are very common — putting most organizations using S3 buckets at risk.
According to Ermetic, every enterprise environment the company studied had at-risk identities, with 90% of AWS S3 buckets vulnerable. A whopping 70% of machines were publicly exposed to the internet with permissions that could be exploited. Some 45%of environments had third party identities whose privileges could be escalated to admin level. In addition, 80% had IAM Users with access keys that had not been used for at least 180 days, but were still enabled.
“Very few companies are aware that data stored in cloud infrastructures like AWS is at risk from ransomware attacks, so we conducted this research to investigate how often the right conditions exist for Amazon S3 buckets to be compromised,” said Shai Morag, CEO of Ermetic. “We found that in every single account we tested, nearly all of an organization’s S3 buckets were vulnerable to ransomware. Therefore, we can conclude that it’s not a matter of if, but when, a major ransomware attack on AWS will occur.”
In a statement to WebProNews, Saumitra Das, Blue Hexagon CTO and Cofounder, said Ermetic’s research highlights the need to detect threats instead of simply trying to fix misconfigurations.
“This report highlights the urgent need to “detect threats” in the cloud and not just focus on misconfigurations,” Das said. “Research from Cloud Security Alliance shows that even if misconfigurations are detected in S3 buckets or IAM access keys not being used for a long time, it takes a while for these to get detected and remediated – sometimes days, weeks and even months. It also highlights that ransomware is not just an on-premises problem but as the pandemic has accelerated cloud migration of workloads it has also accelerated cloud migration for attackers and ransomware criminal operators.”
Das said there are three things companies must monitor, including runtime activity of identities; cloud storage, including read/write patterns; and network activity, which can help companies ascertain when instances are exposed to the internet and their identities misused.
“You cannot guarantee that mistakes like identities being enabled for too long, too permissive, leaked in code will not happen,” Das continued. “They can only be reduced. On the other hand, keeping an eye on active attacks on the cloud infrastructure can thwart attackers from gaining enough privilege and access to ransom the data.”