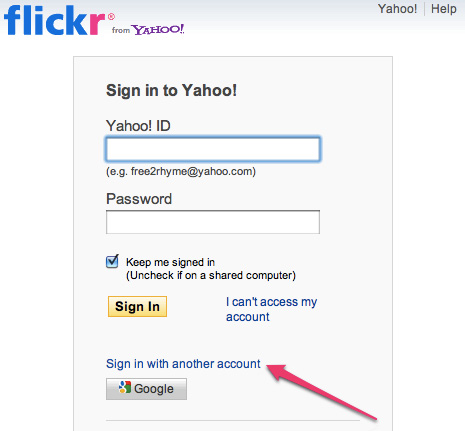
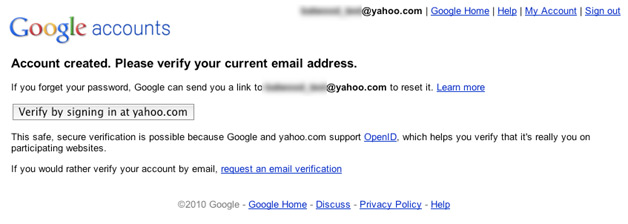
As previously reported, the White House is working on a "National Strategy for Trusted Identities in Cyberspace" or NSTIC, in which it has placed the Commerce Department in charge of an "Identity Ecosystem". The initiative has drawn a mixture of praise and criticism, and judging by our own readers’ comments, there is a whole lot of criticism. More on this here.
Share your thoughts on the White House’s strategy.
We had a discussion on the subject with Chris Messina, Google’s Open Web advocate. Messina was there when the plan was revealed, and is rather knowledgeable in the subject of online identity (besides working for Google, he’s on the board of the OpenID Foundation, and has worked with Mozilla to produce a concept on implementing identity in the browser called "The Social Agent") , which is why we felt he would be a good person to share his views on the strategy.
"As it stands, I can see why people are angry or confused, but, while vague, the NSTIC isn’t as bad as people seem to think — the fact that it’s being run out of commerce means that the government is looking for innovation and competition — not to own these identities," Messina tells WebProNews. "Of course I can’t say what this means about surveillance and security, but anyone who uses a cell phone or hosted email should already understand that they’re susceptible to government wiretaps and data seizure — oftentimes without needing to be informed (Twitter is the rare exception recently). Anyway — if you can pick an identity provider that’s certified to meet certain criteria and that you also trust — that seems win-win to me."
What the government has suggested appears to be the use of platforms like OpenID. " We need a vibrant marketplace that provides people with choices among multiple accredited identity providers – both private and public – and choices among multiple credentials," said Cybersecurity Coordinator and Special Assistant to President Obama, Howard A. Schmidt, upon the announcement of the plan. "For example, imagine that a student could get a digital credential from her cell phone provider and another one from her university and use either of them to log-in to her bank, her e-mail, her social networking site, and so on, all without having to remember dozens of passwords. Such a marketplace will ensure that no single credential or centralized database can emerge."
 "The government’s NSTIC plan is designed to promote OpenID and other existing (and not-even-invented) initiatives," explains Messina. "In fact, the NSTIC was written with input from many of these groups including the OpenID Foundation. It went through an open comment period as well — so it’s not as if many of these concerns weren’t raised before. Since the final draft of the NSTIC hasn’t been released yet, I expect many of them will be reflected in the final draft."
"The government’s NSTIC plan is designed to promote OpenID and other existing (and not-even-invented) initiatives," explains Messina. "In fact, the NSTIC was written with input from many of these groups including the OpenID Foundation. It went through an open comment period as well — so it’s not as if many of these concerns weren’t raised before. Since the final draft of the NSTIC hasn’t been released yet, I expect many of them will be reflected in the final draft."
"The NSTIC calls explicitly for the creation of an ‘identity ecosystem’ — fancy words for saying ‘we don’t want a system where there’s only one identity provider’ (least of all the government!),’ Messina continues. "Now, one of the challenges with creating an ‘ecosystem’ is that you end up with potentially non-interoperable solutions, leading to consumer confusion and frustration (think: ‘Sorry, we don’t accept American Express here’). So while the government intends to rely on private industry to develop the technologies and protocols — such as OpenID — that will enable this ecosystem, I believe that the government has a role in placing pressure on the industry to eventually select a set of standards we can all live with."
"I, for one, would prefer to avoid a government-developed identity standard at a time when industry is rapidly innovating in this space and wants to solve this problem as much as — if not more than — government does," he adds. "But I also know that there are a lot of vested interests that would love to have their pet protocol selected as the gold standard here (pun intended) and that’s going to require leadership, persistence, and an open process so that the best solution(s) to the problem eventually shake out from several years of competition and experimentation."
A common concern expressed by the public has been along the lines of: a single username and password for all sites is a bad idea, and is not secure, compared to having many usernames and passwords.
"The user’s concern is valid," says Messina. "One username and password for everything is actually very bad ‘security hygiene’, especially as you replay the same credentials across many different applications and contexts (your mobile phone, your computer, that seemingly harmless iMac at the Apple store, etc). However, nothing in NSTIC advocates for a particular solution to the identity challenge — least of all supporting or advocating for a single username and password per person."
"In reality, different applications requiring different levels of security, and different behaviors require different kinds of protections," he says. "As Howard A. Schmidt pointed out, for many people, you don’t necessarily want to use the same password that you use for Facebook that you do for your bank. For someone like me, however, where my social media presence is both very important and valuable to me, I want to protect all of my accounts — financial and social networking — equally. So there’s no one-size-fits-all solution, but that’s closer to the reality today — where I as a user often DON’T have a choice about how strong the security deployed to protect my accounts is — versus the future, where we’ll have an ecosystem of identity providers all offering different kinds of protections."
"To restate this point: when I sign up for an account today, why can’t I choose to login in everywhere with my Google account and then rely on Google’s anti-fraud and second factor authentication features to protect my account? Or, if I’d prefer to use someone other than Google, why can’t I use them instead, and rely on, say, their biometric security features?"
"Until a competitive marketplace and proper standards are adopted across industry, we actually continue to have fewer options in terms of how we secure our accounts than more," he says. "And that means that the majority of Americans will continue using the same set of credentials over and over again, increasing their risk and exposure to possible leaks (see: Gawker)."
In the comments section of our previous article, one reader asked who would be responsible "WHEN (not if)" the systems proposed get hacked.
"Going back to my previous point, if we truly arrive at a user-centric ecosystem, then the party that you choose to represent you as your identity provider will be responsible should anything happen to your account," says Messina. "And I hope that people actually choose their identity provider carefully, and based on the steps that they take to secure your account and keep it safe."
"A user-centric model demands that users be in charge of selecting their identity provider, and that this free choice creates a competitive marketplace where identity providers compete for customers," he adds. "If one provider has lax security or onerous identity proofing requirements, the market will ideally reflect that situation by rewarding or punishing them economically, leading to user-positive improvements. Some of this does depend on users having some understanding of what’s at stake when it comes to their online identities and profiles, but just as people safeguard their cell phones today, I think people will feel similarly protective of their online accounts in the future (if they don’t already) and will look for ways to keep those accounts safe and secure."
As we reported before, there doesn’t appear to be anything in the NSTIC indicating that people will be required to use ID systems spawned by the initiative – a point that some people may have overlooked.
"The last thing that I’ll add — which itself is controversial — is that this whole system, at least at the outset, will be voluntary and opt-in," Messina says. "That means that if you don’t want the convenience of not having to use passwords anymore, you won’t have to. If you’re okay rotating your passwords and maintaining numerous discreet accounts across the web, that’s cool too. I don’t think a mandatory system would succeed — at least not without proving its security, stability, convenience, and utility over several years."
"Furthermore, the fact that this initiative is being run out of the Commerce Department, which has an interest in stimulating growth, business, and innovation, means that we hopefully won’t end up with a set of technologies designed only by security wonks that are completely unusable by regular folks, but that the market will see the exploration of a number of different competitive solutions, and from them, a few will stand out as leading the way forward."
"I am hopeful that NSTIC, at the very least, is raising these issues at a critical time on the web — where the future of competition for who owns your identity online is in question," Messina concludes. "My hope is that we arrive at a place where people have a choice, and they can go it alone as steadfast libertarians might prefer, or they can choose to get some assistance from the Googles and Facebooks of the web in dealing with this increasingly important issue."
Speaking of Facebook, any system – existing or spawned from NSTIC – will have a hell of a time competing with Facebook for "owning" users’ online IDs. Facebook has nearly 600 million users worldwide, according to recent estimates, and has a pretty big competitive advantage with its Open Graph and Facebook Log-in features already implanted firmly across many sites around the web.
Comments welcome.

 "The government’s NSTIC plan is designed to promote OpenID and other existing (and not-even-invented) initiatives," explains Messina. "In fact, the NSTIC was written with input from many of these groups including the OpenID Foundation. It went through an open comment period as well — so it’s not as if many of these concerns weren’t raised before. Since the final draft of the NSTIC hasn’t been released yet, I expect many of them will be reflected in the final draft."
"The government’s NSTIC plan is designed to promote OpenID and other existing (and not-even-invented) initiatives," explains Messina. "In fact, the NSTIC was written with input from many of these groups including the OpenID Foundation. It went through an open comment period as well — so it’s not as if many of these concerns weren’t raised before. Since the final draft of the NSTIC hasn’t been released yet, I expect many of them will be reflected in the final draft."